Cyber Threat Hunting
Autonomously hunt for and protect against today’s advanced attacks, threats and vulnerabilities.
Managed Threat Hunting Analysis
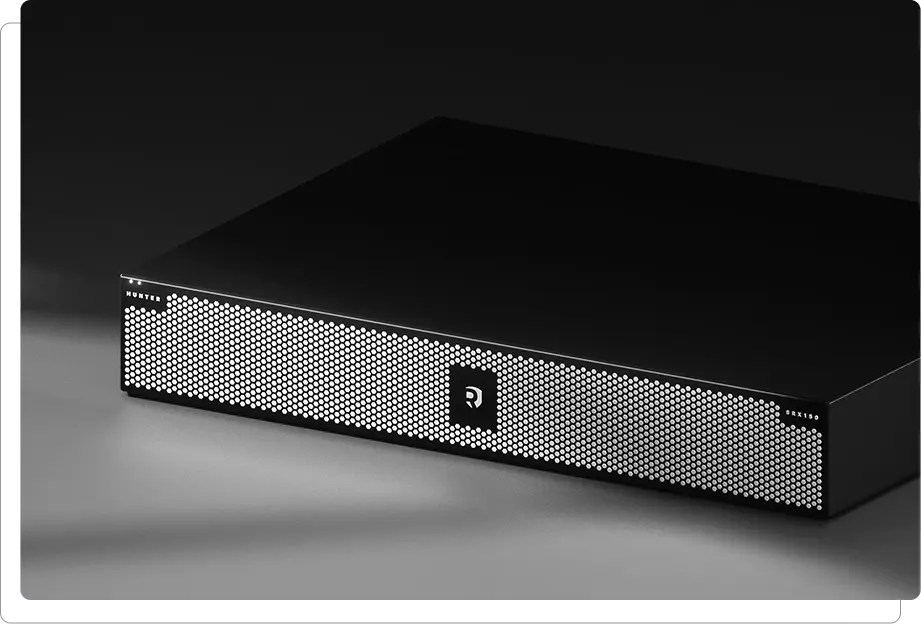
Armed with our solution, organizations have the power of autonomous threat analysis and deep analysis of traffic patterns, user behaviors, and potential vulnerabilities. Our threat analysis software proactively monitors and detects user, application, system and network anomalies.
Our solution works with large datasets of collected information to pinpoint advanced threats and respond to today’s complex cyber-attacks that commonly evade detection. Organizations get full analysis, reporting, details and remediation recommendations for effective cybersecurity against today’s advanced attacks.
Configurations
Our solution is available in 3 different configurations, The SRX150 / 200 / 300 is designed to protect distributed enterprise campus locations and serve as a perimeter firewall for small, medium and large data centres.

Proactive Threat Hunting
Our solution extends and reinforces the security perimeter by covering all the critical dimensions of a modern enterprise.
- Assets
- Users
- Apps
- Network
- Services
- Devices
- IoTs
- Clouds
- Supply Chain
- 3d Party
See our solutions in action through interactive demos
Get a firsthand experience of how our products and platforms can fortify your defenses against modern cyber threads.
